The Future of Secure Access Starts Here
Our mission is to make sure the right people and systems have the right access to the right resources — keeping your business secure, efficient and in control.


Emergency IAM Stabilization After a Breach or Cloud Security Incident
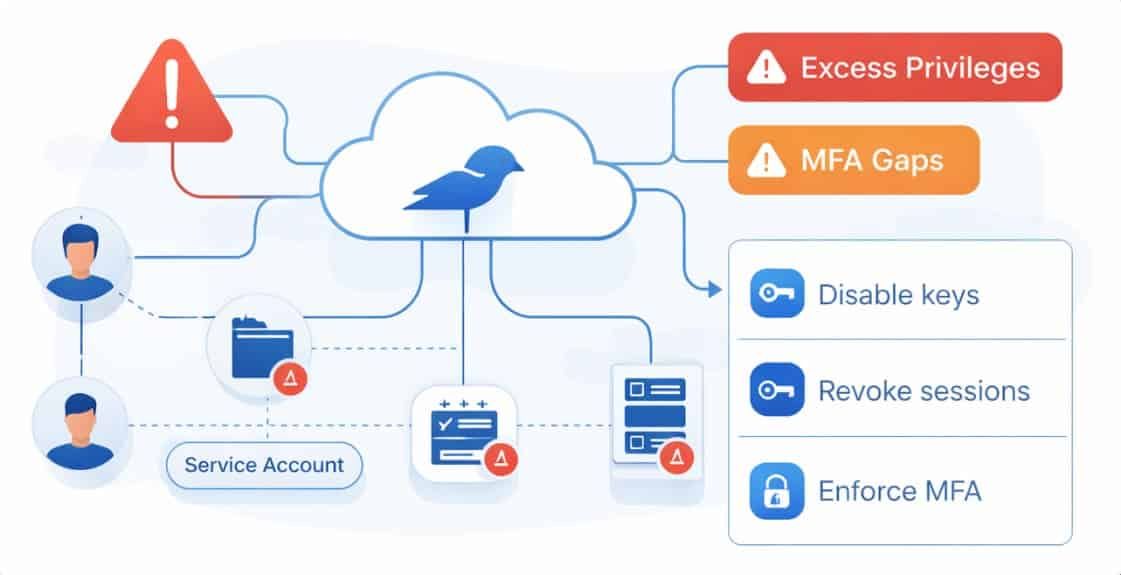
- A security incident quickly escalates into a full-scale business crisis
- Identity and access failures magnify the scope and impact of the breach
- Limited IAM visibility delays containment and remediation efforts
- Legal, regulatory, and customer pressure intensifies almost immediately
Our experts stabilize your cloud IAM in days—not quarters—rapidly regaining control of access, privileges, and identity sprawl so your organization can contain the incident, limit damage, and continue operating without paralysis.
Cyber Insurance Has Become Another Audit
Premiums
continue to rise
Coverage
limits are shrinking
Exclusions
are expanding
Applications are increasingly delayed — or denied outright
We help companies implement the specific security controls insurers expect, easing premium pressure, minimizing exclusions, and eliminating last-minute remediation requests during underwriting and renewal.
Weak Penetration Test Results
Penetration test reports arrive with dozens of findings
Recommendations are often impractical or misaligned with real-world operations
The same issues resurface year after year
We address the root causes behind the findings—not just the findings themselves. Penetration test results become a roadmap, not a checkbox exercise, ensuring remediation meaningfully reduces risk instead of simply closing tickets.
Pre-Audit Pressure or Audit Failure
Industry standards and frameworks (HIPAA, PCI, CIS)
The real cost to the business — time, resources, and revenue
Government regulatory compliance requirements (FedRAMP, CMMC, FISMA, GDPR)
Upcoming audits creating operational slowdowns and distractions
Fundraising and enterprise readiness (SOC2, ISO27001)
Failed audits impacting revenue, credibility, and customer trust
We eliminate cloud IAM permission debt without disrupting day-to-day operations, implementing enforceable least-privilege guardrails that stand up to regulatory scrutiny and give auditors clear, verifiable controls they can approve with confidence.
What do we help with
- A security incident quickly escalates into a full-scale business crisis
- Identity and access failures magnify the scope and impact of the breach
- Limited IAM visibility delays containment and remediation efforts
- Legal, regulatory, and customer pressure intensifies almost immediately
- Premiums continue to rise
- Coverage limits are shrinking
- Exclusions are expanding
- Applications are increasingly delayed—or denied outright
- Penetration test reports arrive with dozens of findings
- The same issues resurface year after year
- Recommendations are often impractical or misaligned with real-world operations
Pre-Audit Pressure or Audit Failure
- Industry standards and frameworks (HIPAA, PCI, CIS)
- Government regulatory compliance requirements (FedRAMP, CMMC, FISMA, GDPR)
- Fundraising and enterprise readiness (SOC2, ISO27001)
- The real cost to the business — time, resources, and revenue
- Upcoming audits creating operational slowdowns and distractions
- Failed audits impacting revenue, credibility, and customer trust
We eliminate cloud IAM permission debt without disrupting day-to-day operations, implementing enforceable least-privilege guardrails that stand up to regulatory scrutiny and give auditors clear, verifiable controls they can approve with confidence.